SG 131/25
CRA implementation accelerates with developments in standards, ENISA pilot projects, guidance and reporting platforms.
Since the European Commission adopted the Cyber Resilience Act on November 20, 2024, and it officially came into effect on December 11, 2024, several activities have been undertaken by:
- European Commission
- European standardization organizations: European Committee for Standardization (CEN), European Committee for Electrotechnical Standardization (CENELEC) and European Telecommunications Standards Institute (ETSI)
- European Union Agency for Cybersecurity (ENISA)
Standardization request
On April 3, 2025, the Standardization Request for the Cyber Resilience Act (CRA) was officially accepted by CEN, CENELEC and ETSI. These European standardization organizations have committed to delivering harmonized standards ahead of the regulatory deadlines.
Cyber Resilience Act: Standardization Request Officially Accepted by CEN, CENELEC, and ETSI
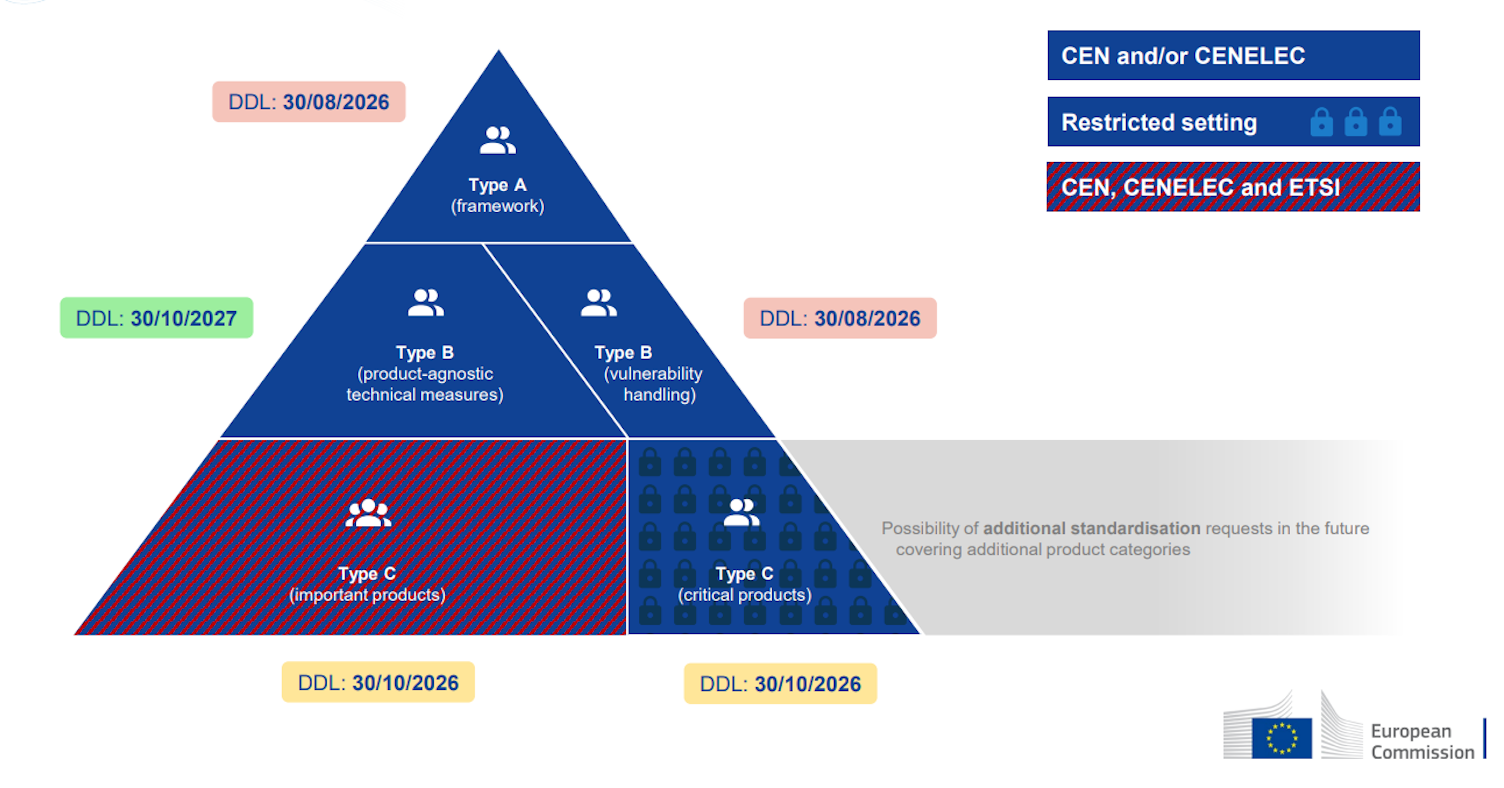
The development of these standards is led by several technical committees, which play a central role in defining harmonized European Standards aligned with the essential cybersecurity requirements defined in the CRA. There are three categories of standards in development:
- Type A standard on cyber resilience principles: covers the first sentence from Annex I: “Products with digital elements shall be designed, developed and produced in such a way that they ensure an appropriate level of cybersecurity based on the risks.” It is expected to be published by August 2026
- Type B horizontal standards: include product-agnostic cybersecurity requirements and vulnerability handling standards. The generic requirements standard is anticipated by October 2027, while the vulnerability handling standard, based on existing ISO/IEC standards, is due by August 2026. Both cover phases like discovery, triage and remediation
- Type C vertical standards for products: specific requirements tailored to certain digital product categories. These standards specify CRA requirements providing presumption of conformity, if followed. They must align with Type A and B principles and are targeted for publication by October 2026
Brightsight is represented in the following Type C working groups:
- CLC/TC 47X/WG 02 – Tamper resistant Microprocessors and Microcontrollers
- CLC/TC 47X/WG 03 – Smartcards and Secure Element Platforms
- CEN/TC 224/WG 17 – Protection Profiles in the context of Secure Signature Creation Devices (SSCD)
CEN CENELEC organized a webinar ‘Standards supporting the Cyber Resilience Act’ for Manufacturers and distributors.
Webinar 'Standards supporting the Cyber Resilience Act'
Feedback on the technical descriptions
Stakeholders were encouraged to submit their feedback on the draft technical descriptions of important and critical products with digital elements before April 18, 2025. In total, 122 detailed submissions from companies, organizations and individuals were received and published on the website of the European Commission:
Technical description of important and critical products with digital elements
By December 11, 2025, the Commission shall adopt an implementing act specifying the technical description of the categories (Article 7(4)).
CRA expert group
The European Commission has established a CRA expert group, comprised of up to ~60 members, including representatives from DG CONNECT, Member States, ENISA and industry/civil society. It supports implementation via advisory input on delegated/implementing acts and guidance documents.
The CRA expert group has held two meetings, covering topics such as:
- Technical descriptions of important and critical products
- Open source software
- Risk assessments
- Remote data processing solutions
- Interplay of CRA and EUCC and RED
Guidance
Many stakeholders seek guidance on CRA interpretation. Some guidance is CRA-mandated, while additional non-mandated guidance is in preparation.
Mandated guidance (article 26) includes:
- Scope definitions
- Support periods for security updates
- Interplay with other legislation
- Criteria for substantial modification of legacy products
Additional non-mandated guidance (CRA expert group) (under development) covers:
- Incident reporting obligations
- Supply chain due diligence
- Risk assessment practices
Interplay between the CRA and the EUCC
In February 2025, ENISA published a proposal on how the EU Common Criteria (EUCC) scheme could support CRA conformity (e.g. ‘presumption of conformity’).
ENISA’s study, ‘Cyber Resilience Act implementation via EUCC and its applicable technical elements’, analyzes how certification through EUCC could demonstrate CRA compliance. It identifies overlaps and gaps, and ENISA has announced pilot projects to update the most-used protection profiles (PPs).
In June, ENISA held webinars exploring this alignment and announced a physical workshop planned for Q4 2025.
Cyber Resilience Act implementation via EUCC and its applicable technical elements
During the EUCC–CRA interplay webinar, ENISA called for conformity bodies (CBs), information technology security evaluation facilities (ITSEFs) and manufacturers to participate in pilot evaluations to test the interplay between EUCC and the CRA.
The main objectives of the EUCC/CRA pilot projects are to:
- Test the EUCC–CRA Interplay: assess whether and how EUCC provides a path to compliance
- Identify gaps and adjustments to PPs and STs
- Validate technical mappings between CRA essential security requirements (ESRs) and the security functional requirements (SFRs) and security assurance requirements (SARs)
- Inform ENISA to update the EUCC–CRA Interplay Report
- Provide recommendations for CRA compliance using EUCC certification
In line with a potential delegated act to establish presumption of conformity with the CRA through an EUCC certificate, the European Commission is examining how this approach could be applied in practice. The ENISA pilot projects play a central role in this exploration. While the Commission does not intend to mandate certification, it aims to enable manufacturers with EUCC-certified products to leverage their certification and benefit from presumption of conformity under the CRA.
The pilots are expected to be completed early Q1 2026.
Interplay between the CRA and the Radio Equipment Directive (RED) Delegated Act
The RED Delegated Act (RED DA) may be repealed, leaving the CRA as the sole horizontal piece of legislation on product cybersecurity. A draft of the Delegated Regulation (EU) 2022/30 is prepared for repeal, with effect from December 11, 2027.
European vulnerability database
ENISA launched the European Vulnerability Database (EUVD) on May 13, 2025. It serves as a centralized platform for actionable vulnerability information, enhancing digital security across the EU by helping entities meet supply chain and vulnerability management requirements under the NIS2 Directive.
EU launches a European vulnerability database to boost its digital security
Single reporting platform
The Single Reporting Platform (SRP) is being developed to facilitate the reporting of vulnerabilities and cybersecurity incidents for products with digital elements, as mandated by the CRA (Article 16). The platform will enable manufacturers to notify the relevant authorities about actively exploited vulnerabilities and severe incidents.
ENISA is tasked with building and implementing this platform, which will support various functionalities, including the handling of notifications as outlined in the CRA. It will also support the management of vulnerability information throughout the product lifecycle.
The reporting obligations for actively exploited vulnerabilities and significant incidents will be enforced on September 11, 2026.
Next steps in CRA
Further guidance will be prioritized on:
- Due diligence in risk assessment
- Substantial modification criteria
- Support periods
- Vulnerability handling and reporting
- Tailor-made products
- Product vs. service distinction
- Spare parts
- Open-source software stewards and licenses
- Software bill of material (SBOM)
- SME support
Brightsight, an SGS company, can assist manufacturers in navigating the complexities of the CRA. We offer comprehensive security evaluation services to assess compliance of digital products CRA requirements, covering a wide range of product categories, including IoT devices, software and connected hardware.
CRA-related services include:
- Training – learn how CRA affects your business, time to market, product design and more
- Gap analysis – identify gaps between your current processes and CRA compliance
- Readiness assessment – includes penetration testing, product security analysis and threat modeling to assess CRA readiness
Link: Cyber Resilience Act
© SGS Société Générale de Surveillance SA. This publication or website is a property of SGS Société Générale de Surveillance SA. All contents including website designs, text, and graphics contained herein are owned by or licensed to SGS Société Générale de Surveillance SA. The information provided is for technical and general information purposes only and offers no legal advice. The information is no substitute for professional legal advice to ensure compliance with the applicable laws and regulations. All information is provided in good faith “as is”, and SGS Société Générale de Surveillance SA makes no representation or warranty of any kind, express or implied, and does not warrant that the information will be error-free or meet any particular criteria of performance or quality.





