Cybersecurity Attack Principles & Incidents

Cybercrime can lead to financial damage running into the billions, data breaches and damage to people’s health.
Everyone loves new technologies. They are used for nearly everything, from communicating and planning, to entertainment. Technology makes our lives safer and more convenient, increases our health potential, and offers us new experiences. But it also makes us vulnerable, can be hard to predict and can have a negative impact on our everyday lives.
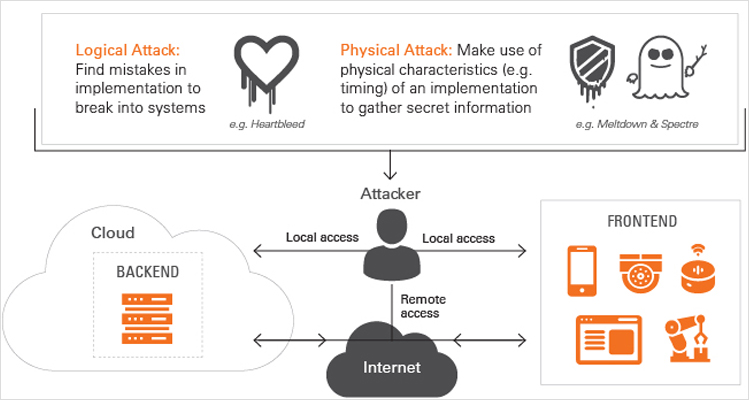
When hackers try to break a system, they carry out implementation attacks on hardware or software, using logical or physical attack principles applied locally or remotely.
Local attacks
Hackers study a specific device to find weak spots and develop ways to exploit them.
Remote attacks
Hackers exploit what they have learnt about devices operating in the field to meet their objectives, such as disclosing personal information, gaining a financial benefit or even impacting people’s lives by compromising safety measures.
Accordingly, devices, as well as IT- and cloud-network equipment – their hardware and software – need to be protected against local and remote implementation attacks.
Semiconductors: Meltdown & Spectre

Meltdown can affect all Intel x386, IBM Power and some ARM based processors and Spectre can affect almost all modern computing platforms. Meltdown and Spectre attacks open access to sensitive memory content.
These hacks were published in 2018. They exploit vulnerabilities in caching implementations, and branch prediction and speculative execution methods, to get access to sensitive information.
Source: NYtimes.com
Medical Devices: Pacemaker

Black Hat 2018: Researchers Billy Rios of WhiteScope and Jonathan Butts of QED Secure Solutions demonstrated how attackers could remotely install malicious firmware on a device used by doctors to control their patients’ pacemakers.
Root cause: Lack of encryption and missing code signatures along the firmware update process.
Source: Wired.com
Consumer IoT: Mirai Botnet

This hack took place in October of 2016, and still ranks as the largest DDoS attack ever launched. The attack was launched from a botnet of IoT devices. Media titans like Twitter, Reddit, CNN, and Netflix were affected. It primarily targets online consumer devices such as IP cameras and home routers.
The hackers leveraged default usernames and passwords of numerous IoT devices to get access and take control over them.
Source: theguardian.com
Industrial: Triton
Hackers deployed malicious software on a Triconex safety controller model (PLC) made by Schneider Electric that enabled them to take over safety instrumented systems of, for example, petrochemical or nuclear plants. These controllers and their associated software are the last line of defense against life-threatening disasters.
The hackers found a “zero-day vulnerability”, or previously unknown bug, in the Triconex model’s firmware. This let them inject code into the safety systems’ memories.
Source: theguardian.com
Automotive: Jeep Hack
Demonstrated in July 2015 by an IBM team. Researchers took total control of a vehicle and were able to accelerate and slow down, as well as turn the wheels and cause the car to veer off the road.
The researchers were able to access the onboard software of a Jeep SUV and exploit a vulnerability in the firmware update mechanism.
Source: electronicdesign.com


